Wireshark alternative ➡️ tcpdump (Linux)
In this blog:
- What is tcpdump?
- Installation.
- Usage.
- Saving captures to a file.
- Filtering output.
- Expressions.
- Understanding the output.
- Packet content.
- The end?
What is tcpdump?
Tcpdump is a command line alternative to Wireshark and runs natively on Linux based operating systems.
The tool is not as feature rich as Wireshark but can be faster and more efficient in capturing and displaying packets, hence why many network admins and security professionals like using tcpdump for quick analysis.
Being a command line tool allows it to be run on remote servers to troubleshoot networks where a gui may not be available. The .PCAP files can then be analysed with Wireshark later.
Most Linux distributions come with tcpdump installed, so your distro might already have it downloaded. To check if you have it, type which tcpdump and the path to the software will be displayed if it is on the system.
 |
| Checking if we have tcpdump installed. |
Installation
To download, open the Linux terminal and type Sudo apt-get install tcpdump, then type your admin password. Sudo stands for ‘superuser do’.
The library libcap (used for packet captures must be on the system too). This will be downloaded as a dependency during install.
To get more information on the tool type man tcpdump to display the manual.
 |
| Manual page for tcpdump. |
Usage
To see what interfaces are available for us to capture packets on, run the command tcpdump --list-interfaces.
 |
| Seeing what interfaces are available. |
The interface any allows us to capture packets on any interface so we can use this.
Run the command sudo tcpdump --interface any.
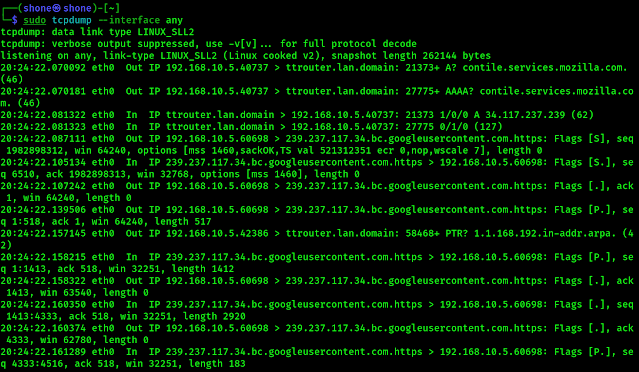 |
| Traffic captured. |
In this instance, I interrupted the process after capturing almost 3000 packets.
You can disable name resolution using -n and port resolution by using -nn.
Tcpdump can also be limited to the number of packets it captures by using the -c<number of packets> flag.
This makes it easier to quickly troubleshoot networks.
Since the domain name servers don't need to be connected to during this kind of scan, the load on the network is less and reduces network traffic.
 |
| Preventing host name and port resolution and limiting packets captured. |
Saving captures to a file
Saving captures to a file is great if you have too many packets to analyse as you can let the program run and once it terminates, you can analyse the results from the file whenever you want.
To save captures to a file, use the -w flag (for writing out).
 |
| Writing our packet capture to a file named packetfile.pcap. |
The file extension .pcap stands for packet capture and allows us to open the file using any packet capture software we want. By default in Kali Linux, the file is opened in Wireshark.
Verbose output
 |
| Verbose output. |
The -r flag lets us read the capture file in the terminal itself.
 |
| Reading the file in terminal. |
Opening the .pcap file starts up Wireshark so we can analyse the results.
 |
| Opening the file in Wireshark. |
Filtering output
You can filter the output in terminal.
For example, if you want to filter by destination IP, type ➡️
tcpdump -r <file_name> dst <IP address>.
I removed the sudo prefix as we are not capturing packets from the network anymore.
 |
| Filtering output by destination IP. |
You can Also filter by source IP by using the src flag. Type ➡️
tcpdump -r <file_name> src <IP address>.
 | |
|
Filtering by protocol
You can filter the output for certain protocols that you want to look out for.
Just type the tcpdump command but add the protocol that you want at the end.
For example, if you want to look out for ICMP packets, type ➡️
sudo tcpdump -i any -c5 icmp.
The interface flag can be shortened to -i.
 |
| Start the command with icmp filter. |
 |
| Pinging Google for tcpdump to pick up icmp packets. |
 |
| tcpdump has captured icmp messages from our connection to Google. |
Filtering by host
 |
| Start the command with host filter. |
 |
| Pinging bbc.com for tcpdump to pick up packets directed at bbc.com. |
Filtering by port
You can filter the output by port by using the port flag and providing the port number you want to filter for. Type ➡️
 |
| tcpdump has captured only packets sent over port 443. |
Expressions can be used to combine multiple filters to fine comb our results even more. They can be simple or complex.
To filter for packets from source IP 143.244.38.136 and port 443, Type ➡️
Sudo tcpdump -i any -c5 src 143.244.38.136 and port 443.
 |
| tcpdump has captured packets sent over port 443 from our specified source IP. |
To filter for packets from destination host wireshark and port 443 OR port 1023, Type ➡️
Sudo tcpdump -i any -c5 "dst wireshark and (port 443 and port 1023)".
 |
| tcpdump has captured packets sent over tcp port 443 or port 1023 and from our specified destination IP. |
Understanding the output
 |
| Flags in tcpdump and their meanings. |
Typical tcp packet ➡️
| Typical tcp packet. |
 |
| Timestamp of the received packet. |
The next part eth0 shows what interface the packet was captured from ➡️
 |
| Interface where packets are being captured from. |
Source and destination IP addresses are shown next with the port number shown after the first IP address. IP is the network layer protocol and represents IPv4. In the case of IPv6, IP6 would be shown ➡️
| Source and destination IP addresses and port number. |
The flags represent what stage the TCP connection is at ➡️
This one below stands for push-ack. The other flags and their meanings can be found above in the table.
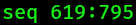 |
| Sequence ID. |
The next part is the Ack Number which is sent from the TCP server to acknowledge that the packet has been received and that it is ready for the next bit of data.
In this case, the Ack Number is 1 as this is the side sending the data.
If this was captured on the receiving side (webserver), the Ack Number would signify the next byte of data being sent in this flow (795 in our case).
 |
| Ack Number shown. |
The window size comes next and refers to the buffer size (bytes) available or remaining in this particular TCP connection.
The buffer available on the receiving side tells the webserver how much data is able to be sent over the wire before the client sends the acknowledgement flag and the connection can continue.
If the buffer size is too low, this indicates that the client is unable to process all the data being sent in time and the server must slow down.
When a buffer size of 0 is advertised by the receiver, the sender stops sending data and starts a persist timer which is used to prevent a deadlock situation wherein the next window size update is lost and the sender has to wait for an update.
When this timer expires, the sender tries to get an ack message and a window size update by sending small packets.
If this continues, the receiver will repeatedly advertise small buffer values which in turn results in a smaller set of data being sent and results in the silly window syndrome which is incredibly inefficient as it sends just a few bytes of data in a TCP segment.
 |
| Window size remaining in this connection. |
The final part of the TCP packet is the packet length, in bytes.
This is the length of the payload data, in bytes. (The difference between the last and first bytes in the sequence number).
 |
| Packet length. |
Packet content
Sometimes checking just the packet headers for source/ destination IPs isn't enough to troubleshoot the network and we must check the packet contents in more detail to find what we need.
To view the contents in hex and ASCII, use the flag -X.
To view the contents in just ASCII, use the flag -A. Type ➡️
Sudo tcpdump -i any -c10 -A port 80.
This command provides us with the packet contents of a http transmission.
 |
| Checking packet content. |
This blog only goes through the basics of tcpdump and barely touches on its vast capabilities.
If you want to learn more about this command line alternative to Wireshark, visit the tcpdump website.





Thank you, super helpful!
ReplyDelete