Setting up Metasploitable lab
In this blog:
- What is Metsploitable?
- Downloading Metasploitable on Virtual Machine.
- Inside Metasploitable.
- What's next?
What is Metasploitable?
Metasploitable is an intentionally vulnerable Linux based
virtual machine that is used to train pentesters and security professionals.
As mentioned, the machine is vulnerable to attacks that are not possible to execute on modern systems and is solely for educational purposes.
Metasploitable should not be able to face the public network due to its vulnerability.
Downloading Metasploitable on Virtual Machine
Download Metasploitable2 here ➡️
https://sourceforge.net/projects/metasploitable/
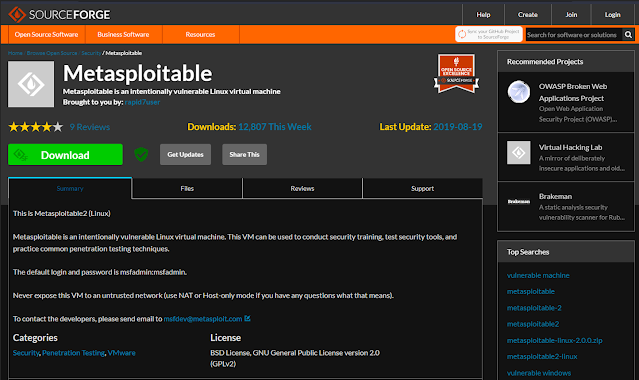 |
| Metasploitable download page. |
 |
| Downloaded zip file. |
 |
| VirtualBox. |
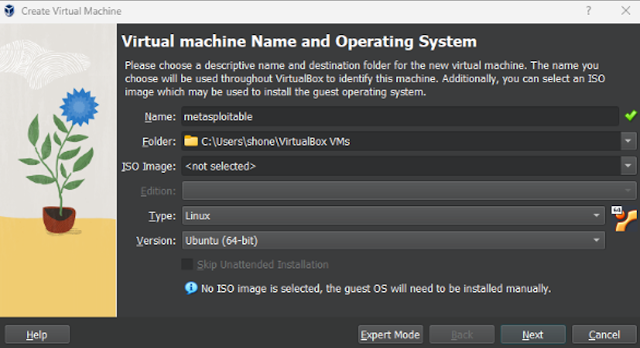 |
| Creating a new virtual machine. |
 |
| Choosing hardware resources for virtual machine. |
 |
| Adding our virtual hard disk. |
Inside Metasploitable
Click b to start booting the vm.
 |
| Booting Metasploitable |
 |
| Inside Metasploitable. |




Comments
Post a Comment